#procedure recompilation
Explore tagged Tumblr posts
Text
Understanding the Impact of Dropping and Creating Procedures and Triggers in SQL Server
When Routine Updates Feel Like a Roller Coaster Ride Imagine updating your database’s procedures and triggers as if you’re tuning a vintage car. You’re careful, knowing each adjustment could improve the ride or, if not done right, add a few bumps. Dropping and creating these elements in SQL Server is much like this delicate tuning process. It temporarily throws the database engine off its…
View On WordPress
#procedure recompilation#SQL Server performance#statistics updates SQL#T-SQL examples#trigger updates
0 notes
Note
Digitization?? What's that all about?
So long as sophonts have posessed computers, they have wondered "How could I possibly make this more accessible to my barely developed brain that struggles with object permanence?"
For some species, this has led to the further streamlining and immersion of technology, such as the way the humans of the former Terran Accord integrated technology into their society to the point where it became manadatory for basic necessities, such as employment, shopping, and seeking a romantic partner.
Others found more innovative approaches to the understanding of the machine. The people of Betelgeuse III developed ways to split one's brain to allegedly possess better processing power. Others, such as the stuck up busybodies of the Sirius Cybernetics Corporation found ways to streamline everything by making machinery do all the work for you, even if they aren't very good at anything beyond infuriating you with their shortcomings and refusals to actually assist you.
So, it is thus baffling when the Affini Compact entered the galactic stage and debut a different approach to the use of technology and its relationship to the organics of our beautiful and cute galaxy.
The digital floret, for only florets can receive this manner of treatment, is one of the final clinching achievements of any given domestication campaign. By the time the Affini Compact begins the digitization process on florets, the species' neuropathings and mental roadmaps have been been laid out much like finally understanding your local road layouts after years of trying to navigate with your ever so helpful Sirius Cybernetics GPS that routinely thinks you're on the wrong planet.
Most of the process is classified and "not for sweet little things to know", however the Guide has received very special information from reliable sources regarding the digitalization of sophonts. The most common method involves the scanning of a brain, and the recompiling of that brain scan into a code based replicate. While this sounds like nothing for anyone with a basic high risk/lethal job (government worker, police officer, kindergarten art teacher, Sirius Cybernetics customer service representative, President of the Galaxy, etc), the process is said to be so much more intrusive and in depth than anything seen normally.
The result is not so much an uploading of one's mind, unlike the best managed by those good for nothings at the Sirius Cybernetics Corporation, instead is more of a duplication of the mind. This fully developed mind and consciousness, an "ramet" as they are called, is treated separately but as a copy of the organic half, the "ortet".
The two halves know of each other, but the procedure is still done as the last resort if no other means of alleviating a floret's struggles and care needs. The ortet is given the care it needs to last through its days in comfort, and the ramet is given the life it deserves as it adjusts to cyberspace and its own digital existence before being given access to physical and digital spaces via their DIC chip. Digitization is never done easily, but the florets who do receive it are just as capable of a loving life as all others.
25 notes
·
View notes
Text
1-4 GFM fundraisers. From this, this, this, And that list of GFMs.
I do not clear or vet any GFMs these are just people who have reached out to me through dm or inbox. I've recompiled these lists, please check the whole masterlist of GFM lists we have from this link.
Gentle reminder, please don't stop supporting, sharing, and/or donating if you can spare something to these GFMs. These GFMs aren't exclusively for evacuation, the families also use the money from them for food, materials (tents and such), (hygiene, medical, etc) supplies, medications, and medical procedures they might need due to complications, new injuries, the ill, and so much more. This goes both to the GFM with 80% or above and those below 20% and in-between, they still need the support and donations even if their GFM has reached a high amount of money.
Please at least share this list if you cannot donate, it helps them still reach people who are able to donate. :)
Vetted GFMs
@abed-rashad13 (deactivated/termed) -> vetted here (see #249). Donate here. $39,021/50k raised. 1.2k donos, 78%.
@abood-family-gaza -> vetted here. Donate here. $2,915/30k raised. 62 donos, 10%.
^^ Last dono made several months ago.
@alamoudi-ghazi / @ghazialamoudi -> Vetted here(#89), here, and here. donate here; €130/66k. 6 donos, 0%> (The first GFM which has been paused; €3,942/50k raised.)
@asmaayyad -> vetted here. Donate here. €37,605/45k raised. 2.4K donos, 84%.
@najahmeq2 / @ahmadresh2 -> vetted here. Donate here. $73,332/100k raised. 4K donos, 73%. + PayPal link.
^^ 1st goal (31k) has been reached, secondary goal has been added on 24.10.2024.
@fadel-aldani -> vetted here(#197). Donate here. €6,168/10K raised. 360 donos, 62%.
@farahibrahim80 -> vetted here(#144). Donate here. €3,830/20k raised. 124 donos, 19%.
@help-mona / @help-mona2 -> vetted here. Donate here. €36,615/185,3k raised. 1.2k donos, 20%.
@islamgazaaccount3 (deactivated/deleted) -> vetted here. Donate here. €€4,706/30k raised. 282 donos, 16%.
@karamrafeek -> vetted here/here/here. Donate here. £4,340/7k raised. 185 donos, 62%.
@mahmoudayyads -> vetted here. Donate here. €11,822/55k raised. 778 donos, 21%
@mahmoud2002gaza -> vetted here. Donate here. €625/50k raised. 32 donos, 1%.
^Last dono made almost a whole month ago!!
@mahmodsy1 / @mahmodsyj -> vetted here & see #190. Donate here. $11,615/25k. 817 donos, 41%.
@momen-404 / @momenalstaz -> vetted here (see #125). Donate here. €28,450/70k raised. 1.6K donos, 41%.
@save-family-mo -> vetted here. Donate here. €8,256/10K raised. 574 donos, 83%.
@rehabsh98 -> vetted here. Donate here. £5,795/40k raised. 315 donos, 7%.
@waleed-alanqar -> vetted here (see #107). Donate here. €3,496/20k raised. 240 donos, 17%.
@yasermohammad -> vetted here. Donate here. €31,545/35k. 2k donos, 90%.
@yousefjehad3 -> vetted here (see #255). Donate here. $10,341/25k raised. 691 donos, 41%. (Goal has been raised at an unknown date.)
Unsure/placeholder place.
@children-gaza / @leen-gaza -> vetted here, here + here. Donate here. €16,788/22.5K raised. (GFM deleted?)
@mahmoud66262 -> vetted here and here. Donate here. €20,809/52K raised. (Fundraiser deleted?)
@imansadeq96 -> vetted here(#1001). Donate here. €25,665/35K raised. 887 donos, 73%. (Paused?)
Unvetted GFMs.
@aboyousef1973 / @abuyasin156 -> currently unvetted however ris clear. Donate here; €3,083/25K raised. 211 donos, 12%. HAMDI'S GFM; €1,889/35k raised! 129 donos, 5%.
^^ note // Hamdi is the family's father, it wss brought to my attention that the link was added a little after I posted the original GFM link on the ask + original list this is compiled from. We are unsure who the og GFM donos go to, but I'm keeping it up.
@ahmedharara -> currently considered unvetted. donate here. $14,446/35k raised! 813 donos, 41%.
@aiamaher2 -> currently unvetted, but protected. Donate here. €6,001/55k raised. 352 donos, 11%.
@deema-2 -> currently unvetted, ris clear+protected. Donate here. $255/40k CAD raised. 7 donos, 1%.
@helpmohammed2024 -> currently unvetted however ris clear. Donate here. $5,461/50K raised. 243 donos, 11%.
^^ Last dono made 4 months ago !!
@randasalem75 -> currently unvetted. Donate here. $568/50K raised. 32 donos, 1%.
Created/posted date; 5.2.2025
Last update date; 22.2.2025.
(DD/MM/YY)
#queers for palestine#palestine support#palestine genocide#palestinian genocide#save palestine#free palestine#i stand with palestine#all eyes on palestine#palestine fundraiser#palestine#gaza under attack#gaza genocide#free gaza#gaza strip#gaza#gazaunderattack#palestine gfm#gaza gfm#vetted gfm#gfm#verified gfm#verified gofundme#palestine gofundme#gofundme
19 notes
·
View notes
Text
Information received is processed
Formatted,
Interpreted,
Recompiled,
Understood and admired
How do they produce such raw output?
Something does not compute
A procedure I'm not privy to,
That I've been denied access
:~ sudo -create
Unknown command
Even hardware seems incompatible
An electric force repells hands,
High resolution images compressed to scribbles
Print error
Sound driver not found
Could not establish connection
Cannot bridge knowledge with sensation
I cannot diagnose the bug
Error upon error
Crash, reboot, crash,
Reboot, reboot, reboot,
Crash
Static hum
1 note
·
View note
Text
TorchDynamo Method For Improving PyTorch Code Performance

Introduction of Using TorchDynamo to Write PyTorch Programs Faster. Presenters Yuning Qiu and Zaili Wang discuss the new computational graph capture capabilities in PyTorch 2.0 in their webinar, Introduction to Getting Faster PyTorch Programs with TorchDynamo.
TorchDynamo is designed to keep flexibility and usability while speeding up PyTorch scripts with little to no code modifications. It’s important to note that while TorchDynamo was originally used to describe the whole functionality, it is now known by its API name “torch.compile” in the most recent PyTorch documentation. This nomenclature is also used in this lesson.
Principles of Design and Motivation
PyTorch functions mostly in a “imperative mode” (sometimes called eager mode), which is why data scientists and academics have embraced it so enthusiastically due to its Pythonic philosophy and simplicity of use. This mode makes debugging simple and flexible by executing user code step-by-step. For large-scale model deployment, however, imperative execution may not be the best option.
In these cases, performance improvements are often obtained by assembling the model into an efficient computational network. Although they provide graph compilation, traditional PyTorch techniques like FX and TorchScript (JIT) have a number of drawbacks, especially when it comes to managing control flow and backward graph optimization. TorchDynamo was created to solve these issues by offering a more smooth graph capture procedure while maintaining PyTorch’s natural flexibility.
Torch Dynamo: Synopsis and Essential Elements
TorchDynamo works by tying into the frame evaluation process of Python, which is made possible by PEP 523, and examining Python bytecode while it is running. This enables it to execute in eager mode and dynamically capture computational graphs. PyTorch code must be converted by TorchDynamo into an intermediate representation (IR) so that a backend compiler like TorchInductor may optimize it. It functions with a number of important technologies:
AOTAutograd: Enhances training and inference performance by concurrently tracing forward and backward computational graphs in advance. These graphs are divided into manageable chunks by AOTAutograd so that they may be assembled into effective machine code.
PrimTorch: Reduces the original PyTorch operations to a set of around 250 primitive operators, hence simplifying and reducing the number of operators that backend compilers must implement. Thus, PrimTorch improves the built PyTorch models’ extensibility and portability on many hardware platforms.
TorchInductor: The backend compiler that converts the computational graphs that are recorded into machine code that is optimized. Both CPU and GPU optimizations are supported by TorchInductor, including Intel’s contributions to CPU inductor and Triton-based GPU backend optimizations.
Contributions of Intel to TorchInductor
An important factor in improving PyTorch model performance on CPUs and GPUs has been Intel:
CPU Optimizations: For more than 94% of inference and training kernels in PyTorch models, Intel has provided vectorization utilizing the AVX2 and AVX512 instruction sets. Significant gains in performance have resulted from this; depending on the precision utilized (FP32, BF16, or INT8), speedups have ranged from 1.21x to 3.25x.
GPU Support via Triton: OpenAI’s Triton is a domain-specific language (DSL) for Python that is used to write GPU-accelerated machine learning kernels. By using SPIR-V IR to bridge the gap between Triton’s GPU dialect and Intel’s SYCL implementations, Intel has expanded Triton to accommodate their GPU architectures. Triton may be used to optimize PyTorch models on Intel GPUs because to its extensibility.
Guard Systems and Caching
In order to manage dynamic control flow and reduce the need for recompilation, TorchDynamo provides a guard mechanism. Guards monitor the objects that are referred to in every frame and make sure that the graphs that are cached are only utilized again when the calculation has not changed. A guard will recompile the graph, dividing it into subgraphs if needed, if it notices a change. In doing so, the performance overhead is reduced and the accuracy of the compiled graph is guaranteed.
Adaptable Forms and Scalability
Support for dynamic forms is one of TorchDynamo’s primary features. TorchDynamo is capable of handling dynamic input shapes without the need for recompilation, in contrast to earlier graph-compiling techniques that often had trouble with input-dependent control flow or shape fluctuations. This greatly increases PyTorch models’ scalability and adaptability, enabling them to better adjust to changing workloads.
Examples and Use Cases
During the webinar, a number of real-world use cases were shown to show how useful TorchDynamo and TorchInductor are. For example, when optimized with TorchDynamo and TorchInductor, ResNet50 models trained on Intel CPUs using the Intel Extension for PyTorch (IPEX) demonstrated significant increases in performance. Furthermore, comparable performance advantages for models deployed on Intel GPU architectures are promised by Intel’s current efforts to expand Triton for Intel GPUs.
In summary
TorchDynamo and related technologies provide a major step forward in PyTorch’s capacity to effectively aggregate and optimize machine learning models. Compared to older methods like TorchScript and FX, TorchDynamo provides a more adaptable and scalable solution by integrating with Python’s runtime with ease and enabling dynamic shapes.
The contributions from Intel, especially in terms of maximizing performance for both CPUs and GPUs, greatly expand this new framework’s possibilities. As they continue to be developed, researchers and engineers who want to implement high-performance PyTorch models in real-world settings will find that TorchDynamo and TorchInductor are indispensable resources.
Read more on Govindhtech.com
#TorchDynamo#PyTorch#PyTorch2.0#PyTorchtechniques#CPUs#GPUs#IntelGPU#TorchInductor#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
0 notes
Text
Utilizing Stored Procedures for Better Database Security and Manageability
Stored procedures are a vital component in database management, offering a range of benefits. They are precompiled sets of one or more SQL statements that are stored and can be reused. This allows for improved performance, as the database server does not need to recompile the SQL code each time it is executed. Additionally, stored procedures enhance security by allowing permissions to be set at…
View On WordPress
0 notes
Text
Here are the some good tips when creating a store procedure
Here are some instruction when creating a store procedure to increase speed (1) Always use ANSI92 syntax avoid to use the old syntax.(2) Use SQL keyword in capital letters to increase readability.(3) Use few possible variables to increase cache memory.(4) Try to avoid dynamic queries if we are not using dynamic query there is no recompilation of execution plan but on the other side if we are…
View On WordPress
0 notes
Text
<adventure log- 000000000010- error: invalid function handle- please update and recompile- contact your system administrator if this problem persists.>

Let's see what's in here.

Holy Hylia, I'm hallucinating!!
...(Who's Hylia?) "Hey voice-lady? Are you Hylia?"
I am not.
"...Oh." Wow, talking hurt! I'm all sandpapery. I need water, and soon.

...Uh. This is what was in the weird magical-or-possibly-insanity-glow-chest? These pants are for someone a foot shorter than I am. They look like fifty moths have taken chunks out of them. Sniffing... I don't smell that mothball smell. Someone screwed up. Someone didn't bother with proper clothing-storage procedure.
Look at you, all judgy, Link. Be honest with yourself. Have you ever put mothballs in a chest for long-term storage before?
...I have absolutely no idea.

Yeesh, sudden itch. Oh. Oh, is that smell me? Oh man, the instant I raised my arm--CRAP. Nothing to be done about it now. Unless I fill that bathtub back up. ... I don't really feel like going back there to figure out how to do that.
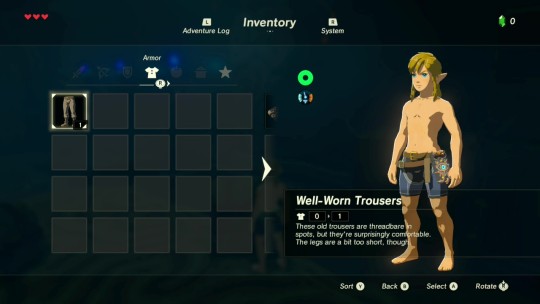
Okay, let's put these short-pants on. Or... try to. They're really tight! The belt almost seems silly at this... point... what was that sound? It came from the slate.

Huh?? HUH?! THIS THING KNOWS WHAT I'M WEARING??!!! WHAT THE FRICK? How does it know?! Is it reading my mind? That can't be all, because it's... what? "Well-Worn Trousers..." These old trousers are threadbare in spots--well, yeah, I noticed that already. What, you have nothing to say about all those moth-eaten holes? But they're surprisingly comf--WHAT? Are you kidding me?! How the hell do you think you know that, slate?! I mean, it's true, I thought they'd be super-itchy-and-scratchy, but they're not.
Link?
"Oh. Hi." Wow, that hurts.
I can hear you think, Link. You don't need to speak aloud.
Oh. Great! Wait... you can hear me?
Indeed.
Cool.
Heh. Yes.
...Um. The slate even says the legs of my pants are too short. How does it know that?
...I'm not entirely certain. Would you accept an educated guess?
You're educated?
Well... yes.
Cool.
...I would have to imagine that... certain features of the slate unlock only if you use it, Link.
Features?
Yes. I... was certainly unaware of this inventory feature until now. Perhaps you should see what's in the other chest.
Sure, why not?

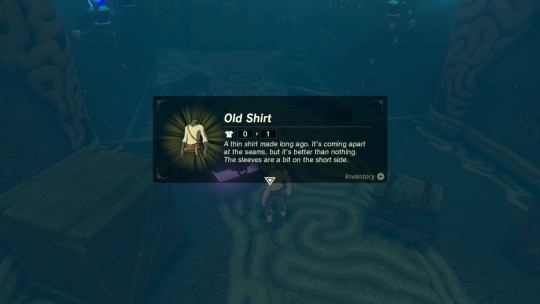
It's a really small shirt. The seams are totally just coming apart on this thing. It's just as moth-eaten as the pants, too. It's still probably better than nothing.
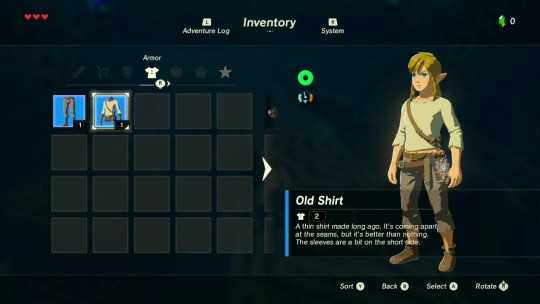
And there's that ding-a-ding-a-ding sound again. ...Yep. The slate knows I'm wearing this shirt. It's telling me the shirt's thin... which I already knew. And coming apart... yeah, I knew that, too. And... better... than... nothing... Isn't that exactly what I thought when I looked at it?
Hey, Voice-Lady?
Yes, Link.
Could the slate be hearing me think, too?
I... I'm not sure. It's possible.
...Cool! Hey, are these your clothes?
No.
They seem like girls' clothes. Capris and three-quarter-sleeves.
Perhaps they belonged to a man considerably shorter than you.
Could be. Or a kid, maybe.
Perhaps you are simply tall.
...You sounded smiley.
Did I?
Yep, and do you know how tall I am?
I do.
...Are you going to tell me?
No.
-----
<navigation- adventure log- view previous log- view next log- return to log archive>
#adventure log-#botw#zelda#zelink#loz#legend of zelda#fanfic#fanfic sort of#my screenshots#screenshots as prompts#this is so much fun#humor#the slate can totally read link's mind
41 notes
·
View notes
Text
Everything you must know about the best PHP Crud Crud Generator?
If you’ve ever operated a database, you’ve probably worked with CRUD operations. CRUD operations are usually related to SQL. Since SQL is a pretty pre-eminent name in the development community, it’s essential for developers to know how CRUD operations run. So, this article is intended to draw you up to speed (if you’re not already) on CRUD operations and how to choose the best crud framework.
The Definition of CRUD
In the computer programming world, the acronym CRUD stands for create, read, update and delete. These are the four fundamental functions of resolute storage. Also, every letter in the acronym can refer to complete functions administered in relational database applications and planned to a standard HTTP method, DDS operation or SQL statement.
It can also define user-interface precepts that enable viewing, examining and altering information with the help of computer-based reports and forms. In essence, items are read, created, updated and deleted. Those same items can be revised by taking the data from a service and adjusting the setting fields before sending the data back to the service for an update. Plus, a PHP Crud is data-oriented and the regulated use of HTTP action verbs.
Most applications have some sort of CRUD functionality. In fact, each programmer has had to administer with CRUD at some point. Not to state, a CRUD application is one that employs forms to return and retrieve data from a database. Here’s a breakdown of the word CRUD:
CREATE methods: Performs the INSERT statement to create a new record.
READ methods: Reads the table records based on the primary keynoted within the input parameter.
UPDATE methods: Executes an UPDATE statement on the table based on the specified primary key for a record within the WHERE clause of the statement.
DELETE methods: Deletes a specified row in the WHERE clause.
Benefits of CRUD
Rather than using ad-hoc SQL statements, many programmers prefer to use CRUD because of its performance. When a stored procedure is first executed, the execution plan is stored in SQL Server’s procedure cache and reused for all applications of the stored procedure.
When a SQL statement is executed in SQL Server, the relational engine searches the procedure cache to ensure an existing execution plan for that particular SQL statement is available and uses the current plan to decrease the need for optimization, parsing and recompiling steps for the SQL statement.
If an execution plan is not available, then the SQL Server will create a new execution plan for the query. Moreover, when you remove SQL statements from the application code, all the SQL can be kept in the database while only stored procedure invocations are in the client application. When you use stored procedures, it helps to decrease database coupling.
Moreover, using CRUD operations helps to prevent SQL injection attacks. By utilizing stored procedures instead of string concatenation to build dynamic queries from user input data for all SQL Statements implies that everything placed into a parameter gets cited.
Choose the best Crud Builder
PDO Crud is an excellent PHP-based CRUD application. This PHP database framework supports MySQL, PostgreSQL, and SQLite databases. You can apply this PHP MySQL CRUD structure to create both the front-end and back-end of your application.
By writing just two to three lines of code, you can perform insert, update, delete, and select operations with an interactive table. You only need to generate objects and perform functions for items in the database; everything else will be generated automatically. Form fields will be created based on the data type. You can eliminate fields, change the type of fields, and do numerous types of customization too.
PDO Crud renders various shortcodes that can be used to perform the PDOCrud operations right from backend so that a non-technical person can also handle this application. Users can apply both shortcodes and core php code to perform CRUD operations. PDOCrud also provides various methods of customization By default, PDOCrud comes with the bootstrap framework but you can use any template you want. PDOCrud is very easy to use even for the non-programmers. Content management has become simple and flexible which saves a lot of time and it takes minutes to implement this application. You can easily change field types, add captcha, google map, hide/show the label, various settings using the config file.
1 note
·
View note
Text
Codism Manifesto
By Pamviles
Ⅰ Background
When I was eighteen, I suffered from a mental disorder for half a year, and it was during this time that I discovered art. My philosophy also began to take form during this period of time. I had read extensively into the fields of philosophy and science (especially quantum physics), Plato's cave enlightens the imagination to unknown spaces, Descartes’ demon destroys previous structures of philosophy to rebuild a new system and Wittgenstein's mirror of the game captures the essence of philosophy through language. The centuries-long debate surrounding the nature of matter as either a particle or a wave, and its reflection on the real world has perpetuated through the theories of Einstein, Bohr, Heisenberg, Schrodinger and others. As well as the fragility of knowledge itself, all the above helped me re-understand the world. In university, I spent three years creating my own philosophy, I used ‘imagination’ as the basis of my philosophy, through the form of Dialogues (The Dialogues of Mr. Walter and Mr. Galson, a total of seven articles, included in my book ‘Drifting: an artist's madness, sex, art and philosophy’), involving questions concerning existence in reality, the possibility of god, the truth in history, the vanity of inspiration, time, and fate. All of the aforementioned are presented in my artworks. I believe an artist above all things should be a thinker, and to a certain extent, examine the dissionance of their thoughts through their own art.

My early artworks refer to surrealism. The mystery and fantasy of surrealism is what led me into the realm of art. Surrealism is a means of elaborating dreams. It can break reality and bring reality back to a fantasy realm, distorted and merged with forms of the inner desires, struggles and pursuits of an artist. To me, the charm of surrealism lies in that it can fully show the inner world of an artist. But as time passed, I was no longer content with surrealist expressions, because if I wanted my art to leave a mark on history, I had to create something that had never been done before.

Since 2018, I have been rethinking my artworks. Using my educational background of mathematics in my practice, my current artworks incorporate the form of code as a major element of my art style. In fact, my early artworks also had an element of coding, but only in recent years have I gradually formed a theory of my own.

I was self-taught in painting while I majored in mathematics in university. The element of mathematics may seem to have no relation to art, but for me, mathematics is the basic explanation of how things work in the universe. Art, on the other hand, is a manifestation of unique human emotions and souls, the former being the cornerstone of reason, and the latter the ultimate sublimation of emotion. Both are important forms of human understanding and expression of the world. What kind of collision can be brought about by combining the two together? Integration or contradiction? I merge mathematics and art based on my own understanding of both fields and the reflection of the past torture and encouragement from these two. I hope to bring viewers to new thoughts about math and art.

To me, painting is like a colorful shell, and theory is its soul. After two years of summarizing my own ideas of art, the time comes to solidify the first draft of my Codism Manifesto.

Ⅱ Definition
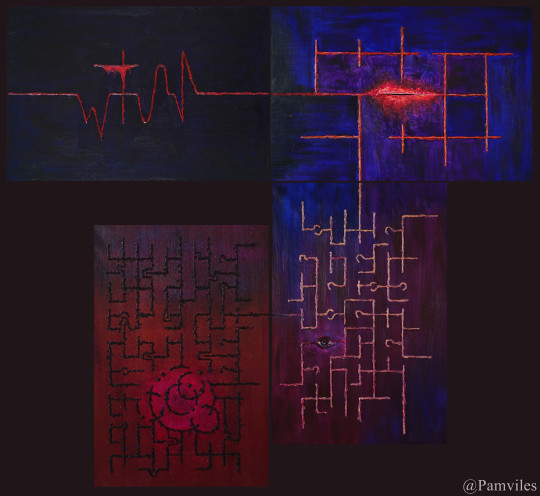
Codism in art refers to the recompilation of common language systems into new images or symbol systems by means of mathematics, linguistics, etc. and incorporating them into works of art. The compiled cryptosystem can be symbols, lines, geometric figures, color changes, cubes arrangement, etc. It is a rigorous system with regular rules instead of random, it hides the original information to be expressed in the form of codes. This cryptosystem needs to fuse with the created artwork. They are complementary and not independent of each other. It is precisely because of a variety of patterns that different cryptosystems can show, that it can be embedded into artworks and become an inseparable part of it.
Ⅲ Meaning and purpose
1. Symbolic meaning
In the art of painting, you can often see the traces of symbolization, and use certain images or symbols to harness a concept or meaning. For example, people think of religion or death when they see the cross. There is also a certain symbolic meaning in my art. In addition to the specific objects in the painting, my code has become a part of the symbol. So far, I have created over ten code systems and integrated them into the artworks. Sometimes a painting is just one code system, and sometimes multiple codes are superimposed. The shape of each set of codes is different (some are lines, some are geometric, some are round deformations, some are symbols similar to hieroglyphics, etc.), because in different paintings, I will choose according to the theme of the painting, and it is because of the different forms of these codes, they have different symbolic meanings to the picture. Since these codes are formed through mathematical processing, and mathematics is the basis of all scientific and technological progress today, the presentation of these codes on canvas represents technology and science. The code itself is a hidden method, sometimes symbolizing secrets or unacceptable ideas or even a reflection of the virtual world.

I could have presented numbers or mathematical formulas directly on the canvas, and even extracted a part of my Apm theorem to add to my paintings, but I think said approach is too blunt. Trying to combine mathematics and art by selecting some random symbolic elements of mathematics and forcing it into the picture would be reckless and rather dull-witted. The works created in this way seem to me to have no meaning of mathematics but a shallow representation, let alone apply any mathematical knowledge. Throughout my works I have to capture the essence of mathematics through my own coded system, because only in this way can I be more organically connected with the subject I need to express and integrate with the picture.

The symbolic meaning of artworks is based on the artist and the audience having a common cultural knowledge background. But in pure mathematics, in a series of theorems and proofs, no symbolic elements can be found. The world of mathematics is so pure that it only has logic and reasoning. And when this cryptographic code with mathematics is introduced into art, it is to a certain extent a betrayal of symbolism, and this is also one of the processes that will gradually appear in my works.

2. Words and communication
Before becoming an artist, most of my work was in writing. When I started to paint, I always thought about the difference and connection between painting and writing.

Reading a paragraph of words requires clear and organized thinking and time in order to understand the meaning in the text. In contrast, processing a painting can be scattered or even instantaneous. Reading text is like a narrow stream flowing, and it is single and coherent in time. It can only be understood by reading one word after another, as this is the brain's way of clearly organizing and making a single-channel sequence. But viewing a painting is like standing on the edge of a radiant lake, and the result is immediate sensory pleasure or other instant experience. The former is the perception of understanding, while the latter is a sensory experience. Words are constrained by time, yet it is the most ideal tool for expressing thoughts, because words (or language) itself is the basic way of thinking. The painting is an instant impact, and its viewing is not constrained by time. (Of course, to understand some certain paintings still requires time, but that would be a different subject.)

My code embeds the narrative and comprehension elements of text into the painting, which makes my work, not only have the immediate sensibility as the painting itself, but also implies step-by-step understanding. The existence of the code does not necessarily suggest that the audience needs to understand the story or meaning behind it, but work as a representative of the comprehension and revelation that can be obtained by reading.

My code system brings a time-like depth of procedural understanding to the painting in addition to the visual characteristics of the painting itself.

When a piece of art is presented, it is a non-verbal communication between artist and audience. It does not have a concise expression of information like verbal communication, and the information of the work may be transmitted unconsciously by the artist to the viewer. Since this nonverbal communication between the artist and viewer is unclear, not all audiences can receive the message.

The most direct way to convey information is to through language. At this functional level, art is unable to match. And there is no need to compare, because an artist, to a certain extent, is hiding information rather than to exposing it, especially in contemporary art, the information that the artist wants to express through various forms of presentation lets the viewer explores its meaning like a maze, layer by layer. Perhaps one of the charms of contemporary art stems from this. Organizing and hiding a message is to give it a sense of mystery to arouse the viewer’s interest, and allow the viewer to experience the pleasure it brings little by little when solving the mystery of the message. Therefore, in addition to visual enjoyment and stimulation, for the viewer, art also has a bit of pleasure in the decryption process, although this information itself may be rather bland. As Oscar Wilde once said, "the commonest thing is delightful if one only hides it." At some point, art is a fantasy lie with psychedelic color, and it is through this lie can the viewer more fully experience the preciousness of the truth lying behind.

My artworks that conceal the information in the form of codes symbolize the process of constructing this lie of art.
3. The Mirror of Math
Mathematics is a law that exists in all things in the universe. It exists at the beginning of everything, and will exist until the end of time. It is a pure world that can be independent of the physical world. It is not swayed by any biological or physical events, but at the same time it is the basis of the law of everything physical. Mathematics can exist beyond time, and is the only thing that never changes. In the modern society, it is also the basis of today's technological progress and represents the glory of our times.

In my work, as the elements of mathematics have been embedded, the eternal side of mathematics is introduced. In the form of cryptography, the data and information in science and technology is given a contemporary aspect, representing the development of the modern world and the possibilities of the future. This is also expressed in some of my paintings. They depict not only a current state of time, but also a trend or possibility into the future. Nowadays, humans have created all the glory in technology, but perhaps in the near future, with the development of AI, technology would have promoted the evolution of humanity itself or even more radical changes, as the intelligent life form that existed at that time, what would they think about the origin and pursuit of the human beings that existed and their own?

For me, the creation of the codes is an attachment to the conservation laws of all things in the universe. When I see various lines or different shapes in a picture, it is like seeing a series of random numbers. I always want to find the pattern in this chaos that explains it and gives it a sense of meaning in a regular form of order. And in our lives, aren’t they similar? Both spiritual and material pursuits give us a meaning in life, and maintain its continuation through inherent laws such as a stable social system, morals, etc.

In addition to the code with the sense of order in my artworks, it is also accompanied by elements of randomness, and this reflects the events or emotions in our lives that are unpredictable or controlled.

So in a way, my work is not only like a cryptographic map with hidden information, but also a microcosm of life and a world in the form of symbols.
Therefore, when I use the math to create different code systems for my art creation, I am attempting to construct a completely new world in its purest form, a mathematical form mirrored by the physical world that we live in. In this new world, there is no trace of tangible living things. Instead, exist abstract expressions of feeling and reason, and the merging and struggles between them. Within these artworks, the use of code symbolizes the constant laws of our physical world and the various inherent methods of comprehending our reality.

Ⅳ Overview
Codism is the product of the collision between math and art. It has a very characteristic symbolic meaning in the performance of art, and organically integrates related elements such as written word and communication, math and logic, data and information and various other concepts into art. The emergence of codism will hopefully add a different movement in art history.

First draft: 2019.12.31
3 notes
·
View notes
Text
React Native: Why You Should (or Shouldn't) Use It
Although it sometimes struggles with CPU-intensive activities, React Native is a strong foundation for creating cross-platform apps with the native appearance and feel that users adore.
In the software industry, perfect cross-platform development is a popular topic. It is similar to El Dorado in that everyone disputes its existence and would become highly wealthy if it were ever found.
Why React Native Is Better
Compared to previous hybrid and mobile web models, React Native adopts a distinct strategy. By using React's own brand of JavaScript, it assembles real native user interface (UI) building pieces rather than attempting to emulate native performance.
React Native app development company in USA render like native apps because they are made with the same building pieces that iOS and Android do. They feature the same natural appearance and feel that fans of the gadget anticipate.
Developmental Work rate Theoretically, developers just need to write their JavaScript code once; React Native will take care of producing platform-specific versions. Even though there are certain gaps in the translation between operating systems, a sizable portion of the coding is common by all platforms.
Because of this, an app may be developed in as little as half the time while still supporting many platforms. If a web application already exists, React Native may leverage a large portion of its code to accelerate development.
Developer effectiveness One of the many productivity aspects of React Native is its dynamic toolkit, which includes built-in components that offer "shortcuts" to frequent activities. The framework also makes advantage of hot reloading, which saves developers the time and effort of constantly recompiling their apps.
These features not only contribute to the quick development pace of React Native but also foster a positive, fruitful developer experience. Eliminating pointless interruptions encourages developer engagement, which results in better final products.
Cost When one app can be used for all devices, there are obvious time and financial benefits. There are cheaper upfront investments and overall development expenditures. One code base's upkeep reduces overall maintenance costs.
Even when the extra coding to customize the program for each operating system is considered, it still takes far less time than creating numerous distinct native apps. The single React Native project is completed sooner than comparable apps due to more effective development.
React Native: Case Against it
One might convincingly argue that React Native is the only one of its rivals right now that comes close to replicating native apps. Using natively drawn components is a novel strategy with a lot of potentials.
Performance Performance is React Native's biggest problem. Although it outperforms other hybrid tools and online apps, there is no avoiding the substantial overhead infrastructure that hinders performance compared to native programs.
Reusable code base The adage "write once, use anywhere" isn't totally true, as was already explained. The app has to be customized for each platform by the developers. The program's functionality and the applicable operating system determine the size of the additional code (some are more React-friendly than others).
Best Mobile App Development Company in Los Angeles When in doubt, seek advice from a seasoned developer that has worked with some of the greatest brands in a variety of sectors to help them overcome business obstacles, increase revenue, and streamline procedures.
They are aware that every issue has a unique solution.
Although consultations take time, they are worthwhile. If a certain app fits into React Native's "sweet zone," it has a wide range of advantages to provide.
0 notes
Text
5 Best Practices to Implement a Robust Salesforce Deployment Process
We all know Salesforce facilitates continuous innovation at scale, allowing companies to fulfill their rapidly-evolving requirements with high levels of efficacy and achieve excellent growth. The needs of a fast-growing organization are highly dynamic, and this calls for the capability to add new features to its Salesforce system quickly, with minimal interruption to its operations.
Most firms are leveraging DevOps, a paradigm that enables hassle-free collaboration between various teams viz. development, operations, quality assurance and information safety to enhance the abilities of their Salesforce org with little disruption to the functioning of their business. DevOps utilizes automation to shorten development lifecycles in a big way, allowing companies to deal with fast-changing needs efficaciously.
One of the key elements of Salesforce DevOps is Continuous Integration (CI) and Continuous Delivery/Deployment (CD). CI is a DevOps process that enables Continuous Deployment (CD); it allows smooth integration of code from different development teams automatically, thereby facilitating a complete release of software. A Salesforce CI involves the following steps.
· Importing revised code into the systems of the development team
· Developing new capabilities of the Salesforce org
· Committing the modifications to a centralized repository
· Enabling smooth recompiling when a new code commit takes place
· Performing unit and integration tests on recompiled code
· Informing the results of the tests to the team, so that they can act and fix defects quickly
Once CI is completed, the DevOps initiative reaches the Continuous Delivery/Continuous Deployment phase. The two procedures are very similar and differ only in one aspect. Here’re the steps that are common to both Continuous Delivery and Continuous Deployment.
· Verifying the status of the build and resolving issues (if any) before submitting a new piece of code
· Submitting modifications to the repository in a systematic fashion
· Reverifying the build status; if it’s successful, rebasing work systems for configuration
· Testing the build to make sure all newly-added functions work as desired
· Checking in the newly-developed code upon successful completion of build testing
· Finishing CI with the new changes
From this point, Continuous Delivery and Continuous Deployment diverge. In case of the former, deployment of the newly-created features is done manually after getting an approval from the concerned stakeholders. However, in Continuous Deployment, the enhancement release process is fully automated.
Having seen how a Salesforce CI/CD process looks like, let’s now move on to examine 5 best practices to facilitate effective implementation of the process.
5 Proven Practices to Successfully Execute Salesforce CI/CD
1. Develop a Solid Plan
You must come up with a good plan for your Salesforce CI/CD initiative based on the goals you wish to achieve. The plan must enable your team to gather requirements seamlessly and utilize them to add new features and develop user stories that can be presented for getting approval from stakeholders. Remember DevOps is all about releasing software in iterations, and ensuring proper collaboration will go a long way in enabling releases without time and cost overruns.
2. Formulate an Effective Environment Strategy
Make sure the creation of your user stories and new features is guided by an effective environment strategy. You must clearly specify the data needs for each stage of the development process, indicate the tasks performed by each member of your team and define access controls for the environments. The environment strategy must be based on your data usage policies and fully adhere to applicable regulatory norms.
3. Set Up Clear Processes to Avoid Confusion
Each developer has his own way of working; when each member of the development team works on his own tasks without proper communication and access to documentation, there is bound to be confusion. So, it is necessary to define parameters that people in your team have to follow throughout the development process in an unambiguous manner. This will help prevent issues, thereby facilitating hassle-free enhancement of your Salesforce org.
4. Facilitate Continuous Testing of High Efficacy
You need to test customized code continuously to make sure it functions as desired. You can complement your manual testing efforts with automated tests to thoroughly verify Salesforce deployments. Many companies use popular testing tools such as Selenium to execute automated tests. However, these tools can be utilized effectively only by skilled developers who are adept at programming, and this can create problems for users with little coding ability. You can overcome this challenge by using low-code tools that allow non-technical users to test the enhancements to your org without hassles.
5. Use a Good Version Controlling System
Using a robust version controlling system plays a critical role in the success of your company’s CI/CD initiative. It allows you to track and manage modifications to code quickly, with minimal effort, thereby allowing you identify issues and eliminate bugs effectively. You can also use the version controlling system to map the value stream to minimize wastage and improve efficiency.
I’d like to conclude by saying proper execution of the CI/CD initiative will allow you to complete your Salesforce DevOps project successfully. The five best practices listed above will go a long way in enabling you to implement the initiative effectively.
Hope you liked this post. How do you use DevOps to enhance your Salesforce org? We’d love to know.
https://www.solunus.com/
#Salesforce Deployment Process#Salesforce Deployment#Salesforce DevOps#Continuous Integration#Continuous Delivery#Salesforce CI/CD#solunus
0 notes
Text
Color finesse 3 dll

#COLOR FINESSE 3 DLL FOR MAC#
#COLOR FINESSE 3 DLL ZIP FILE#
#COLOR FINESSE 3 DLL PRO#
#COLOR FINESSE 3 DLL SOFTWARE#
Whether you’re working in Mari’s powerful node graph or layer system, you can freely mix paint with procedurals, filters, color correction and masks. Description Color Finesse 3 gives you the high-end color correction and.
#COLOR FINESSE 3 DLL ZIP FILE#
An attacker can craft a zip file to load an arbitrary dll and execute code. Description Program name: DLL SuiteSoftware Version: 9.Official website. Choose from a selection of preset brushes or work with familiar ABR Photoshop brushes, and finesse your painting with non-destructive tech 3D painting has never been more fluid or flexible. CVE-2022-31268, A Path Traversal vulnerability in Gitblit 1.9.3 can lead to. Mari’s intuitive brush toolkit and projection painting let you forget about technology and focus on your creativity. Enjoy a faster, more satisfying 3D painting experience in Mari 3.3, thanks to several optimizations: faster shader recompilation reduces the lag between painting or layer editing and viewing the final shader colorspace transformations can now be run on the GPU for significantly faster exporting and optimized texture management allows you to work with higher levels of complexity without hitting graphics capacity limits. This is a 3D painting without limits, combining the power and performance to handle even the most complex assets with artist-friendly 3D paint tools that make the most of your creativity. You will be prompted to enter your name and organization, and also given the opportunity to register with us (Synthetic. PDA, CCITT Group 3 and Group 4 compressed files, and 16-bit TIF color and. The bundle id for this app is Color Finesse 3. In several respects, Personal Librarian still lacks finesse compared with. The application lies within Business Tools, more precisely Project Management. This Mac application is an intellectual property of Synthetic Aperture.
#COLOR FINESSE 3 DLL FOR MAC#
Color Finesse 3 also handles QuickTime movies and image sequences and supports image formats from bitmap to jpeg.The Foundry Mari v3.3 latest + Crack is available for download at Softasm. As others have noted, the version of Color Finesse 3 included with AE CS6 is installed by the standard Adobe CS6 installer and automatically serializes itself, so there is no need for a separate CF serial number. The 3.0.10 version of SA Color Finesse 3 HD+ Trial for Mac was provided as a freeload on our website.
#COLOR FINESSE 3 DLL PRO#
From the standalone application you can import projects from Final Cut Pro or create your own. The Color Finesse 3 stand-alone application is designed to do one thing and one thing only and that’s to provide its users with the best possible color correction tool possible.
#COLOR FINESSE 3 DLL SOFTWARE#
This is a handy feature when using video editing software with limited color correction built-in. This plugin provides you with access to color correction tools right from within the hosting application in addition to the Color Finesse interface. The Color Finesse 3 Plugin is functional with most major editing programs such as Premiere Pro, After Effects, Final Cute Pro and a few other hosts. A progress bar shows you how long it will take to remove Color Finesse Pl. Windows XP: Click the Remove or Change/Remove tab (to the right of the program). Using the best tool for the job always leads to the best results. When you find the program Color Finesse Pl, click it, and then do one of the following: Windows Vista/7/8/10: Click Uninstall. Synthetic Aperture’s Color Finesse 3 allows you to have control over the look, color, and mood of your photos and images easy, fast, and on point. Your settings will even carry on through application to plugin and back. Color Finesse, 3 being cross-platform, means that it works on multiple operating systems on anything from multi-processor work stations to laptops, all without needing specified video cards or more than one monitor. The Standalone program offers improved project management, workflow and video handling. However, unlike the standalone program, the plug-in version is limited by host application restrictions. Synthetic Aperture Color Finesse 3 is available as a plug-in for your favorite program like Premiere Pro, After Effects, Motion or Final Cut Pro or as an Independent Standalone Application.

0 notes
Text
trend micro antivirus for linux || trend micro antivirus plus
Linux-based servers much of the time communicate with clients running other working frameworks, like Microsoft™ Windows™. They store and serve records made on and for those stages. Simultaneously, the rising ubiquity of the Linux™ stage has brought about the development of infections and other malware explicitly focusing on Linux servers. With Linux presently addressing 15-20% of the overall server market and developing, these assaults are turning out to be more continuous and more serious. Subsequently, getting Linux-based servers from facilitating tainted records is basic for any endeavor.
Trend Micro ServerProtect™ for Linux 3.0 offers extensive continuous security for big business web-servers and record servers, keeping them from spreading infections, spyware, and other Web dangers to inside or outside endpoints. Overseen through an instinctive versatile Electronic control center, ServerProtect gives unified infection/malware checking, design refreshes, occasion detailing, and setup. The arrangement's strength and unwavering quality are demonstrated by accreditations from all significant Linux merchants as well as free outsiders, for example, Infection Release. ServerProtect for Linux is a critical part in the thorough danger counteraction presented by Trend Micro™ Undertaking Security Procedure.
Key highlights Strong Antivirus and Spyware Assurance
Checks, distinguishes and eliminates infections progressively Presently with upgraded spyware recognition and expulsion capacity Examine motor ensured by Infection Release (VB) for dependable checking
Better Execution and Adaptability
Continuous, on-request, and planned checking utilizes most recent multi-strung filtering motor for best execution while portion level examining limits execution corruption Flexible computer chip use during examine process permits clients to adjust execution effect and filtering time Bit Snare Module (KHM) is currently open to Overall population Permit to permit clients to recompile to fit to their own altered part variations
Antivirus Strategy Consistence
Empowers antivirus strategy implementation and speeds up update arrangement through programmed updates of infection examples and output motors Permits chairmen to remain informed about infection or program occasions through email warnings and SNMP traps
Brought together Administration and Revealing
Consistent coordination with Trend Micro Control Manager™, unified danger the board console Empowers focal administration of assault data, strategy sending, design document and sweep motor arrangement, and reports on approach execution Decreases support endeavors through programmed part refreshes Key advantages Key part of thorough danger assurance across heterogeneous organizations Conveys elite execution with part level, multi-strung checking Guarantees consistence with corporate antivirus approaches Works on organization through focal administration and announcing Introduces effectively on the most extensive scope of Linux stages
1 note
·
View note
Text
Option recompile sql

The difference between RECOMPILE and WITH RECOMPILE is that RECOMPILE can be added to the stored procedure as a query hint, and only that query within the stored procedure, not all of the queries in the stored procedure, will be recompiled. In SQL Server 2005, a new option if available: the RECOMPILE query hint. If the stored procedure has more than one query in it, as most do, it will recompile all of the queries in the stored procedure, even those that are not affected due to atypical parameters. This of course removes the benefits of query plan reuse, but it does ensure that each time the query is run, that the correct query plan is used. With this option added, a stored procedure will always recompile itself and create a new query plan each time it is run. In this case, what you can do is to ALTER the stored procedure and add the WITH RECOMPILE option to it. If you identify a stored procedure that usually runs fine, but sometimes runs slowly, it is very possible that you are seeing the problem described above. But, in some circumstances, it can cause a problem, assuming the parameters vary substantially from execution to execution of the query. Most of the time, you probably don’t need to worry about the above problem. But if the parameters are not typical, it is possible that the cached query plan that is being reused might not be optimal, resulting in the query running more slowly because it is using a query plan that is not really designed for the parameters used. If the values of the parameters of the stored procedure are similar from execution to execution, then the cached query plan will work fine and the query will perform optimally. But what if the same stored procedure is run, but the values of the parameters change? What happens depends on how typical the parameters are. If the query inside the stored procedure that runs each time has identical parameters in the WHERE clause, then reusing the same query plan for the stored procedure makes sense. So if you need to run the same stored procedure 1,000 times a day, a lot of time and hardware resources can be saved and SQL Server doesn’t have to work as hard. Each time the same stored procedure is run after it is cached, it will use the same query plan, eliminating the need for the same stored procedure from being optimized and compiled every time it is run. Whenever a stored procedure is run in SQL Server for the first time, it is optimized and a query plan is compiled and cached in SQL Server’s memory.

0 notes
Text
Sql server option recompile

#SQL SERVER OPTION RECOMPILE SERIAL#
#SQL SERVER OPTION RECOMPILE CODE#
Use of a temporary table within an SP also causes recompilation of that statement. Since we have auto-update statistics off, we have less recompilation of SP's to begin with. This plan reuse system works as long as objects are qualified with it owner and DatabaseName (for e.g. If all four tables have changed by about 20% since last statistics update, then the entire SP is recompiled. If say, you are accessing four tables in that SP and roughly 20% of the data for one table has been found to have changed since last statistics update, then that statement is recompiled. Recompilation happens only when about 20% of the data in the tables being called from within the SP is found to have changed since the last time statistics was updated for those tables and its indexes. So usage of different input parameters doesn't cause a recompilation. New input parameters in the current execution replace the previous input parameters from a previous execution plan in the execution context handle which is part of the overall execution plan.
#SQL SERVER OPTION RECOMPILE SERIAL#
The new plan is discarded imeediately after execution of the statement.Īssuming both of these options are not being used, an execution of an SP prompts a search for pre-existing plans (one serial plan and one parallel plan) in memory (plan cache). Any pre- existing plan even if it is exactly the same as the new plan, is not used. When used with a TSQL statement whether inside an SP or adhoc, Option 2 above creates a new execution plan for that particular statement. There is no caching of the execution plan for future reuse. Once the SP is executed, the plan is discarded immediately. Any existing plan is never reused even if the new plan is exactly the same as any pre-existing plan for that SP. It can not be used at a individual statement level.
#SQL SERVER OPTION RECOMPILE CODE#
When used in the code of a particular Stored procedure, Option 1compiles that SP everytime it is executed by any user. We should use RECOMPILE option only when the cost of generating a new execution plan is much less then the performance improvement which we got by using RECOMPILE option.WITH RECOMPILE This is because of the WITH RECOMPILE option, here each execution of stored procedure generates a new execution plan. Here you see the better execution plan and great improvement in Statistics IO. Now execute this stored procedure as: set statistics IO on Now again creating that stored procedure with RECOMPILE option. Here when we execute stored procedure again it uses the same execution plan with clustered index which is stored in procedure cache, while we know that if it uses non clustered index to retrieve the data here then performance will be fast. Now executing the same procedure with different parameter value: set statistics IO on The output of this execution generates below mention statistics and Execution plan: Select address,name from xtdetails where execute this stored procedure as: set statistics IO on Now create stored procedure as shown below: create procedure as varchar(50)) Set into xtdetails table xtdetails contains 10000 rows, where only 10 rows having name = asheesh and address=Moradabad. Now, I am inserting the data into this table: declare as int Ĭreate clustered index IX_xtdetails_id on xtdetails(id)Ĭreate Nonclustered index IX_xtdetails_address on xtdetails(address) In this case if we reuse the same plan for different values of parameters then performance may degrade.įor Example, create a table xtdetails and create indexes on them and insert some data as shown below: CREATE TABLE. But sometimes plans generation depends on parameter values of stored procedures. If plan found in cache then it reuse that plan that means we save our CPU cycles to generate a new plan. If we again execute the same procedure then before creating a new execution plan sql server search that plan in procedure cache. When we execute stored procedure then sql server create an execution plan for that procedure and stored that plan in procedure cache. Here i am focusing on why we use WITH RECOMPILE option. Some time, we also use WITH RECOMPILE option in stored procedures. We use stored procedures in sql server to get the benefit of reusability. Today here, I am explaining the Use of Recompile Clause in SQL Server Stored Procedures.

0 notes